CS 40 - Lecture 14

Cay S. Horstmann
Lecture 13 Recap

- Java: Industrial-strength programming language
- Greenfoot: environment for developing Java
programs
- Image manipulation: Edit image by getting/setting
pixels
Personal Computer Security

- Who attacks your computer?
- What are their motivations?
- How do they do it?
- What can you do to protect yourself?
Example: The Morris Internet Worm

- November 2, 1988 (!)
- Program attacked most of the several thousand (!) machines on the
internet
- Exploited “buffer overflow” problem in
finger
daemon
- Attacked trusted neighboring computers
- Due to programming error, consumed most of computers' resources
- Released by a Cornell University student, Robert Morris...
- ...who was sentenced to 3 years probation, 400 hours community service
and a $10,500 fine
Buffer Overflow

- Program code and data are all contained in memory
- Any memory block (called “buffer”) must have some maximum
size
- What happens if the buffer is filled with data that is longer than the
buffer?
- Java: An error occurs
- C/C++: If no explicit check, the memory beyond the buffer is
overwritten
- Exploit: Send excessively long data block over network, overwrite part
of the program
Lab 1. Buffer Overflow
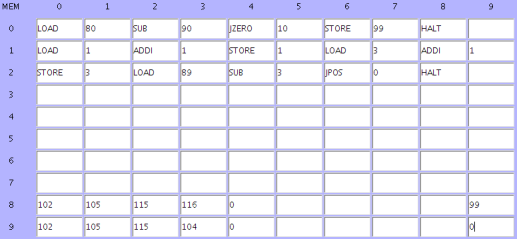
- Password check in simple computer (Program in next slide)
- Password encoded in Unicode (f = 102, i = 105, s = 115, h = ...)
- User provided password put in memory locations 80, 81, etc.
- Correct password in locations 90, 91, ..., 98
- When checker is finished and passwords match, location 99 is 0
- When passwords don't match, location 99 is some non-zero value
Lab 1. Buffer Overflow
Lab 1. Buffer Overflow
You are the attacker. Suppose you can fill locations 80, 81, etc., and
there is no overflow check. Fill them so that the password check will
succeed.
What do you fill them with? ActiveLecture.org
Attack Categories
- Attacker's problem: How to run code on your computer
- Pathways:
- Make network connection to your computer and send data that
exploits software vulnerability (such as buffer overruns)
- Trick you into launching an application
- Cause malicious script to run on your computer
Launching Applications
- Clickin on app launches it (e.g. Alice, Firefox)
- Clicking on document launches associated app
- E.g. click on Word file to launch Office
- Installer = Special application that installs another app
- Once an application is installed, the operating system trusts it
- Don't click unless you trust it
Example: The Image That Isn't

- What happens when you click on
attractive_person.gif?
- Launches associated viewer (Paint, Firefox—app depends on your
computer)
- Except...when it is was really
attractive_person.gif.exe!
- Too bad Windows hides known file extensions in order to be
“helpful”
- Never left-click on attachments. Ok to right-click and choose Open
With
Scripts
- Script = program in a simple language, usually tied to an
application
- Examples: VBScript (Microsoft Office), JavaScript (web browser)
- Purpose: Automation of repetitive task (Office macros)
- Easy to carry out powerful tasks (erase file, send email)
- Runs automatically upon certain events that are not usually perceived
as dangerous:
- Visiting a web page
- Opening an email message or attachment
Example: The Love Bug

- May 2000: Internet was flooded with email messages with subject line
“I LOVE YOU”
- When opened in Microsoft email reader, script ran immediately (without
asking)
- Script opened address book and sent I LOVE YOU messages to everyone
- No damage (except having to explain that you didn't actually love all
those people)
- Authored by Onel de Guzman, as part of his computer science master's
thesis. (He didn't graduate.)
Example: Samy
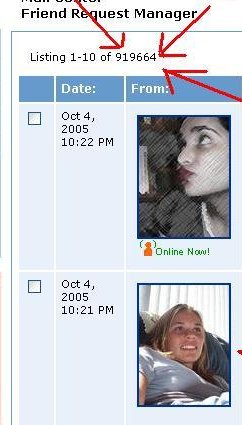
- Scripts in browser run automatically (JavaScript, Java applets)
- In theory, they are safe, but subtle browser bugs can make them unsafe
- October 2005: Samy “cross-scripting attack” added a million
MySpace users to the author's friend list. You were added if you viewed
the page of one of the “friends”
- Samy Kamkar sentenced to 3 years probation, 90 days community
service
Blocking Attacks

- Network connections:
- Use Firewall
- Install OS patches
- User action:
- Use anti-virus software and pay for updates
- Think before you click
- Read those security warnings
- Script:
- Use Firefox, not IE
- Install patches
- Consider NoScript extension
Lab 2. How Did the Attack Work?
Read this article: http://www.eweek.com/article2/0,1895,1940747,00.asp.
How did the malware get to the user's computer?
ActiveLecture.org
- Kazaa installed it over the network
- The user installed it
- A script installed it
Attacker Types
- Graffiti artists—bragging, no theft or vandalism
- Thieves—look for account numbers, interfere with financial
transactions
- Zombie masters—use your computer for their own purposes (usually
sending email spam)
- Spammers—display ads on your computer, watch your
browsing/shopping
- Spies—invade your privacy, spy on your email, communication, etc.
- Vandals—destroy your data
Threat: Botnets
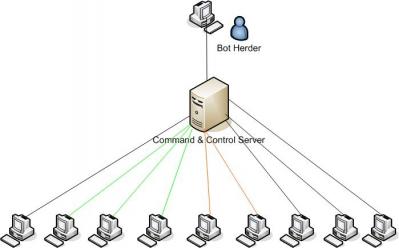
Threat: Stealing Personal Data
- Infected computer monitors keystrokes, web pages
- Looks for credit card numbers, CVV codes, bank account numbers,
addresses, social security numbers
- Botnet operators sell data to criminals: http://www.cio.com/article/135500/
- Data used to pump/dump stocks, purchase goods, clean out bank
accounts
- Who pays? With credit cards (but not debit cards), you are protected.
With electronic funds transfer, you are not: http://www.iht.com/articles/2005/02/15/business/netbank.php
Lab 3. Categorize Attacker
- Read through this article: http://www.eweek.com/article2/0,1895,2214103,00.asp
- Once your computer is infected with the fake software, how will you be
harmed? ActiveLecture.org
- Vandalism
- Theft of money
- Having your computer turned into a Zombie
- Spam
- Spying / Theft of your data
What Can You Do?
- Install a reputable security product...
- ...but only one!
- Install all operating system and browser patches
- Think before you click!
- Never run as administrator unless you install software
- Read those security dialogs. If in doubt, don't agree.
- Consider Linux, Mac OS X or Windows Vista over Windows XP
Reminders

- Homework #5 due tonight
- Project proposals due tonight











