CS 40 - Lecture 6

Cay S. Horstmann
Lecture 5 Recap

- method: a named sequence of instructions
- parameter: an input to a method
- method call: a statement that contains the method name and
parameter values
- calling a method: setting the parameters and executing the
method instructions
How Was the Homework?
ActiveLecture.org
- Too easy/boring
- Just right
- Too hard/confusing
- Not done yet
- What homework?
Thanks for your feedback!
Computing for Congressmen
- Computing touches the lives of all citizens
- Examples: voting machines, spam mail, credit scoring, data privacy,
music sharing, etc. etc.
- Stakeholders (hardware vendors, , banks, copyright holders, etc. etc.)
don't give unbiased advice
- Need a basic understanding of computer science to understand
risks/rewards
History of Voting Equipment

Voting Machines

- Automates the counting of ballots
- Scanner: Voter marks ballot or punch card, machine tallies them
- Direct recording: Voter pushes buttons, machine tallies button
pushes
- Voter verifiable paper trail: Machine prints paper tape (behind glass
window)
Positive Aspects
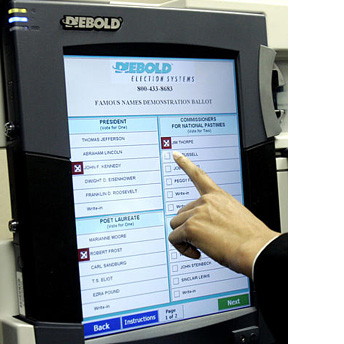
- Direct recording: Can reduce undervote by alerting voters to skipped
selections
- Some machines help people with various disabilities (but others
actually make it harder...)
- Generally faster results, greater accuracy than counts by humans
What Can Go Wrong?

- 2000: Hanging chads, overvotes
- 2006 Sarasota, FL: In heavily democratic county, 18,326 voters (13%)
didn't vote for either house candidate...or did they? (Undervote in
neighboring Manatee County: 2 percent). Republican won seat with 363
votes.
- 2007: Team lead by UC Davis Prof. Matt Bishop breaks into every CA
voting machine (http://www.sos.ca.gov/elections/voting_systems/ttbr/red_overview.pdf)
Lab: Find the Flaw
- Load VotingMachine1.a2w and click
Play.
- Click on the cow and the hampster [sic] to vote for dems and reps. Each
click is one vote. (They didn't have donkeys and elephants.)
- Click on the toaster to get the result.
- What is the subtle flaw in this machine? (Spoiler on next slide.)
- Answer in ActiveLecture.org.
Lab: Find the Flaw #2
- Spoiler: Click Play, then click twice on the cow, twice on the
hampster, then on the toaster.
- Load VotingMachine2.a2w and click
Play.
- What is the subtle flaw? Hint: look into the source code for the
toaster's sayWinner method.
- How can you demonstrate the flaw to a voting official who can't read
code?
- Answer in ActiveLecture.org.
Lab: Find the Flaw #3
- Load VotingMachine3.a2w and click
Play.
- What is the even more subtle flaw? Hint: look into the source code for
the toaster's methods.
- How can you demonstrate the flaw to a voting official who can't read
code?
- Answer in ActiveLecture.org.
Attack Scenarios

- Voting machine vendor favors one party???
- Rogue employee at voting machine vendor?
- Partisan poll workers
- Fraud during data consolidation
- Setup errors, particularly with complex elections
- Defects in hardware/software
Computer Science
- Impossible to prove that software works correctly
- Impossible to prove that software hasn't been tampered with
- Developing/testing high reliability systems is expensive, time
consuming
- Independent verification/fallback is indispensable
Why the Resistance?
- Voting machine vendors
- need to make a profit
- have not been held to high standards
- Election officials
- have limited funds
- are not fond of recounts
- are not always non-partisan
What is Being Done?
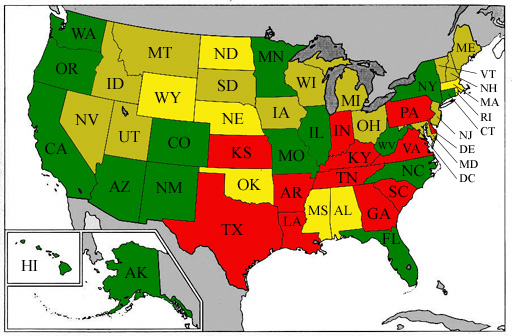
- Activist groups had some success
- http://verifiedvoting.org
(founded by Stanford professor David Dill)
- Many states require independent paper trail
- Some states require mandatory random spot checks
- Sep 2007: HR 811 (sponsored by Rush Holt, D-NJ) considered by
congress
Reminders

- Homework #1 is due today (submit in eCampus)
- Solutions for labs are in eCampus









